Suspect Commits
This feature is only applicable for error issues. Other categories of issues (such as performance issues) do not support this feature.
Suspect commits show you the most recent commit to the code in your stack trace. In the suspect commit information, we include the author of the commit and the pull request in which the commit was made.
When you've enabled suspect commits, we can tie together issues with the commits made in your code repository, including the following information:
- Files observed in the stack trace
- Files touched by those commits
- Authors of those files
Suspect commits and suggested assignees are then displayed on the Issue Details page in sentry.io, as shown below.
Enable Suspect Commits
In order to see suspect commits, you have to first upload source maps, (or your platform-specific files for mapping transformed source code to the original source). Check out the docs for your specific platform) to learn more. Be aware that Sentry will not display suspect commits for issues that were created prior to your integration being set up.
1. Connect a Repository Using Integrations
Suspect commits can be enabled using the following integrations:
In sentry.io:
- Go to Settings > Integrations.
- Click the integration you’d like to use.
- Configure the integration if you haven’t already.
- Add the repository you'd like to use.
2. Set Up Code Mappings
Sentry will automatically try to set up code mappings on Python and JavaScript projects for organizations with the GitHub integration installed. However, you can still manually add code mappings if you choose to do so. Support for other languages and other source code integrations are planned.
- Go to Settings > Integrations > [Integration] > Configurations.
- Click the "Configure" button.
- Click the "Code Mappings" tab.
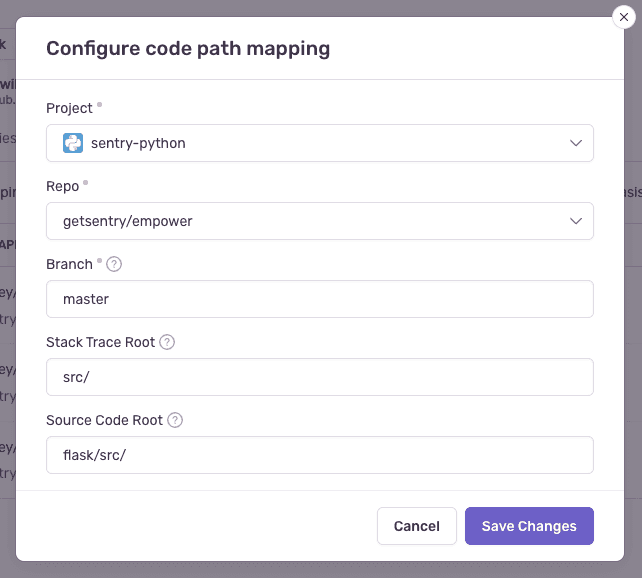
- Set up a code mapping for each projectRepresents your service in Sentry and allows you to scope events to a distinct application.for which you want to enable suspect commits. To create a new code mapping, click Add Mapping.
- Fill out the form, then click Save Changes. Each form field is described below.
Code Mapping Form Fields
- Project (required) - The Sentry projectRepresents your service in Sentry and allows you to scope events to a distinct application..
- Repo (required) - The GitHub or GitLab repository associated with the Sentry project above. If you have more than one repository being used per Sentry project, you'll need multiple code mappings.
- Branch (required) - The default branch of your code we fall back to if you don't have commit tracking set up.
- Stack Trace Root and Source Code Root (optional): See below for information on determining these values.
Stack Trace Root and Source Code Root
The following information is only valid for platforms which use traditional file paths. Platforms with package names (such as Java, Cocoa, and Flutter) require additional steps.
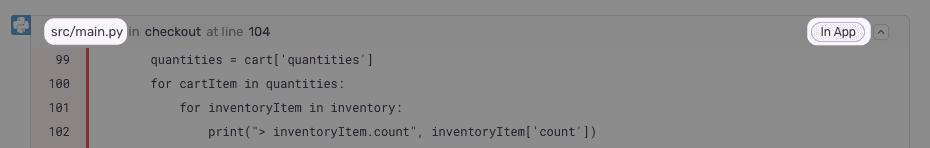
First, navigate to a stack trace that you wish to map. Find an In App frame, which is denoted by a bubble on the right side of the frame. The filename will be shown as the first piece of text at the left hand side of the frame header. In this example, it is src/main.py.
If you aren’t sure, you can look at the event JSON by clicking on the {} button in the event header. Find the text in the frame's filename.
Next, locate the file seen in the stack trace with your source code provider (e.g. GitHub). In this example, the path is flask/src/main.py (empower is ignored since it is the name of the repo).
Compare the file path from the stack trace with the path found in your source repository. In this example, the src/ folder in the stack trace matches the flask/src folder in the source code. Using that information, set the Stack Trace Root to src/ and the Source Code Root to flask/src/. This tells Sentry to replace all file paths beginning in src/ with flask/src/ when searching for the source code.
For best results, we recommend always providing a non-empty value for the Stack Trace Root when possible.
The first frame in the stack trace is considered suspect when looking at them top-down. If the first frame is not in-app, the next frame is considered suspect.
UI Walkthrough
Follow along with the animated gif below to see how to integrate your GitHub account and repository.
How It Works
When you have a GitHub/GitLab integration and valid code mappings, Sentry will look at the stack trace of an issue and collect all in-app frames. For each in-app frame, Sentry checks the blame info for the exact file and line number. If the most recent commit is less than 1 year old, we consider it a suspect commit.
Suspect Commits Without Integrations
You can send us your commit data manually if:
- You don’t want Sentry to connect to your repository.
- Your organization doesn't have a GitHub or Gitlab integration.
- Your integration has gotten disconnected.
Sentry will attempt to find suspect commits via your GitHub or GitLab integration by default. If this fails and you've set up the manual process, Sentry will fall back to using the release commit data to find suspect commits.
Missing Suspect Commits
There are a few reasons why an issue might not have suspect commits:
- The issue doesn't have a stack trace or doesn't have any in-app frames.
- The stack trace doesn't have any in-app frames that match the code mappings.
- The stack trace doesn't have any in-app frames with recent commits (less than 1 year old).
- The code mappings for the projectRepresents your service in Sentry and allows you to scope events to a distinct application.are incorrect.
- The issue was created prior to the integration being set up.
Limitations
- If auto-assignment is enabled but the Suspect Committer is not in the Sentry organization, we will not be able to auto-assign the issue to them.
Our documentation is open source and available on GitHub. Your contributions are welcome, whether fixing a typo (drat!) or suggesting an update ("yeah, this would be better").